Aws:IAM:AccessAnalyzerPolicyGeneration
⚠️ この記事は最終更新から1年以上が経過しています。情報が古い可能性があるためご注意ください。
目次
80.AccessAnalyzerポリシーの生成
CloudTrailログを分析して、ポリシーを生成してくれる機能
https://docs.aws.amazon.com/ja_jp/IAM/latest/UserGuide/access-analyzer-policy-generation.html
権限不足だとCloudTrailに、[eventName:Decrypt][errorCode:AccessDenied]が沢山でるので注意!!!
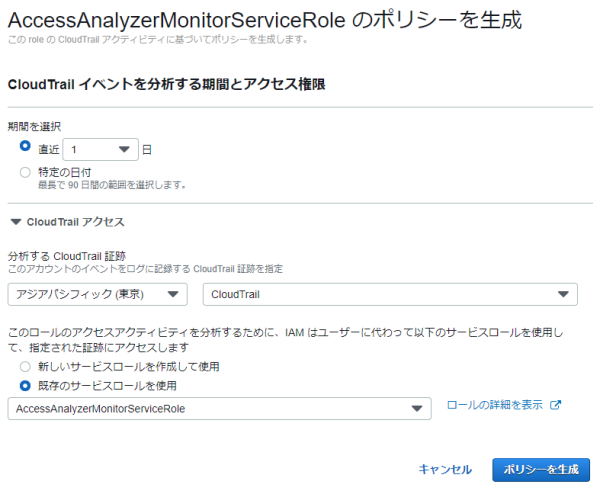
IAMロール作成
信頼関係
- ポリシーサンプル
-
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Service": "access-analyzer.amazonaws.com" }, "Action": "sts:AssumeRole" } ] }
インラインポリシー(AccessAnalyzerMonitorServiceRolePolicy)
- IAMロールポリシーサンプル
-
{ "Version": "2012-10-17", "Statement": [ { "Action": "cloudtrail:GetTrail", "Resource": "*", "Effect": "Allow" }, { "Action": [ "iam:GenerateServiceLastAccessedDetails", "iam:GetServiceLastAccessedDetails" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "s3:GetObject", "s3:ListBucket" ], "Resource": [ "arn:aws:s3:::[CloudTrailバケット名]", "arn:aws:s3:::[CloudTrailバケット名]/*" ], "Effect": "Allow" } ] }
CloudTrailのS3バケット側に追加する設定
- S3バケットポリシーサンプル
-
{ "Version": "2012-10-17", "Statement": [ { "Sid": "PolicyGenerationBucketPolicy", "Effect": "Allow", "Principal": { "AWS": "*" }, "Action": [ "s3:GetObject", "s3:ListBucket" ], "Resource": [ "arn:aws:s3:::[CloudTrailバケット名]", "arn:aws:s3:::[CloudTrailバケット名]/*" ], "Condition": { "StringLike": { "aws:PrincipalArn": "arn:aws:iam::[アカウントID]:role/AccessAnalyzerMonitorServiceRole" } } } ] }
CloudTrailのS3バケットがCMK暗号化されていた場合
- キーポリシーサンプル
-
{ "Version": "2012-10-17", "Statement": [ { "Sid": "Enable IAM User Permissions", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::[アカウントID]:root" }, "Action": "kms:*", "Resource": "*" }, { "Sid": "Allow use of the key", "Effect": "Allow", "Principal": { "Service": "cloudtrail.amazonaws.com" }, "Action": [ "kms:Encrypt", "kms:GenerateDataKey*", "kms:DescribeKey" ], "Resource": "arn:aws:kms:[リージョン名]:[アカウントID]:key/*", "Condition": { "StringEquals": { "aws:SourceArn": "arn:aws:cloudtrail:[リージョン名]:[アカウントID]:trail/[証跡名]" } } }, { "Sid": "Allow use of the key for AccessAnalyzer", "Effect": "Allow", "Principal": { "AWS": "*" }, "Action": "kms:Decrypt", "Resource": "*", "Condition": { "StringLike": { "aws:PrincipalArn": "arn:aws:iam::[アカウントID]:role/AccessAnalyzerMonitorServiceRole*", "kms:ViaService": "s3.*.amazonaws.com" } } } ] }
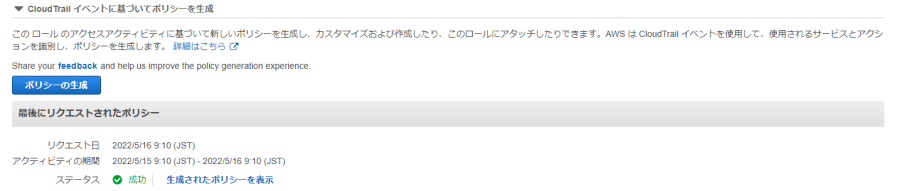
ポリシーの生成
Aws/IAM/AccessAnalyzerPolicyGeneration.txt · 最終更新: by 127.0.0.1
コメント